A Complete Guide About Bypassing Android SSL Pinning
Introduction
Are you concerned about the security of your Android device and want to know how to bypass SSL pinning? Look no further! SSL pinning is a crucial security feature that ensures secure communication between an app and server. However, there may be times when it becomes necessary to bypass this mechanism. In this blog post, we will explore everything you need to know about bypassing SSL pinning on Android, including different methods and their pros and cons. So let’s get started!
What is SSL Pinning?
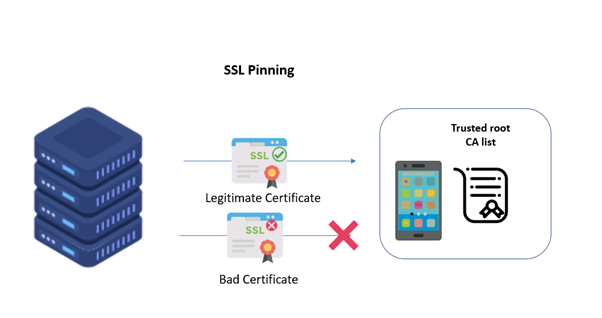
SSL Pinning is a security measure used by mobile applications to ensure that the communication between the client and server is secure, private, and not compromised. In SSL Pinning, apps use a specific SSL certificate or public key to verify the authenticity of the server they are communicating with.
This process ensures that no man-in-the-middle attacks can intercept and modify data being exchanged between an app’s client and its designated server. As such, it provides additional protection against potential vulnerabilities in TLS/SSL protocols.
The practice of SSL pinning has become increasingly popular over recent years as more users rely on their mobile devices for sensitive transactions such as financial information or personal data sharing. However, it also poses challenges for developers who need to test APIs or debug problems related to network connections.
Therefore, some developers seek ways to bypass this security feature temporarily during testing or debugging sessions using tools like Frida which allows them to inject custom code into running processes on Android devices without modifying their source code.
The Different Methods of Bypassing SSL Pinning on Android
There are a number of ways to bypass SSL pinning on Android devices, but they all come with their own set of advantages and disadvantages. One common method is using a tool called Frida, which injects code into the target app and allows you to inspect and modify its behavior.
Another approach involves modifying the APK file itself by either patching it manually or using an automated tool such as Lucky Patcher. This can be effective in some cases, but it’s also more time-consuming and carries a higher risk of breaking the app.
A third option is intercepting network traffic using a proxy like Burp Suite or Charles Proxy. This allows you to inspect and modify any data that passes through the device, including SSL-encrypted traffic.
There are also commercial solutions available that claim to bypass SSL pinning automatically without requiring any technical expertise. These tools can be convenient for non-technical users but may not always work reliably.
Each method has its own unique strengths and weaknesses depending on your specific use case and level of technical expertise. It’s important to carefully evaluate your options before proceeding with any particular approach.
How to Bypass SSL Pinning on Android
To bypass SSL pinning on Android, there are several methods you can use. One of the most popular ways is by using a tool called Frida. This open-source framework allows for dynamic instrumentation of apps and can be used to intercept and modify network requests.
First, you need to set up Frida on your device or emulator. Once installed, connect your device to your computer via USB and run the command “frida-ps -U” in your terminal to list all running processes on the device.
Next, find the process ID (PID) of the app you want to bypass SSL pinning for and run “frida -U -l
The Pros and Cons of Bypassing SSL Pinning
Bypassing SSL pinning on Android can be a useful technique for developers and security researchers, but it also has its drawbacks. Here are some of the pros and cons of bypassing SSL pinning.
On the positive side, bypassing SSL pinning allows developers to test their applications in real-world scenarios where certificate validation is not enforced. This can help them identify potential vulnerabilities before they become a problem. It also enables security researchers to analyze network traffic and find weaknesses that could be exploited by attackers.
However, bypassing SSL pinning can also make your device more vulnerable to attacks. By disabling certificate validation, you open up your device to man-in-the-middle (MITM) attacks, which can allow hackers to intercept sensitive information like passwords or credit card numbers.
In addition, bypassing SSL pinning may violate the terms of service for certain apps or websites, making it illegal or unethical in some cases.
Whether or not you should use this technique depends on your specific situation and goals. If you’re a developer testing an app or a researcher looking for vulnerabilities, it might be worth exploring. But if you’re just trying to get around security measures put in place by legitimate apps or services, think twice before taking this approach.
How to Protect Your Device from Being Compromised
Protecting your device from being compromised is essential to ensure the safety of your personal data and privacy. The following are some effective ways to prevent SSL pinning bypass attacks:
1. Keep Your Device Updated: Regular software updates can help keep your device secure by patching vulnerabilities that could be exploited by cybercriminals.
2. Install Antivirus Software: Installing reputable antivirus software on your Android device can provide an extra layer of security against malware, viruses, and other types of malicious programs.
3. Use Strong Passwords: Creating strong passwords for all accounts is essential in preventing unauthorized access.
4. Avoid Public Wi-Fi Networks: Public Wi-Fi networks may be convenient but they are often unsecured which makes it easy for hackers to intercept sensitive information such as login credentials or financial details.
5. Be Cautious When Downloading Apps: Always download apps from reputable sources like Google Play Store, and read reviews before downloading any app.
6. Enable Two-Factor Authentication (2FA): 2FA adds an additional layer of protection when logging into accounts by requiring a second method of authentication like a code sent via SMS or email.
By following these simple steps, you can significantly reduce the risk of having your device compromised through SSL pinning bypass attacks or other similar methods used by cybercriminals to gain unauthorized access to your personal data and information
Conclusion
Bypassing SSL pinning on Android can be a useful tool for developers who need to test their apps or for users who want to access restricted content. However, it is important to keep in mind the potential risks and drawbacks of doing so.
By taking the necessary precautions such as using a trusted VPN service, avoiding unsecured Wi-Fi networks and keeping your device up-to-date with security patches, you can reduce the risk of compromising your device’s security while bypassing SSL pinning.
Remember that while bypassing SSL pinning may give you temporary relief from restrictions, it can also make your device vulnerable to attacks. So use this technique carefully and only when strictly necessary.




